Security Enhanced Mobile Operating System (SEMOS)
The Security Enhanced Mobile Operating System, or SEMOS for short, is a project being designed for a Samsung Galaxy Nexus, running Android 4.3.x. The device will be using an Operating System (OS) that is tailored specifically for heightened security. Tungsten Industries is the sponsor for the project, and would like to create a platform for Android based devices that delivers the security and control a user ought to have.
Starting from an Android core OS, based on the Android Open Source Project (AOSP) with SELinux, we will determine the feasibility of a secure mobile operating system. Our current goal is to study and implement three specific research topics: Mandatory Access Controls (MAC) using Multi-Category Security, Automated Encrypted Cloud Storage, and Remote Service Log Checking & Retrieval. Long term we wish to create a stable, secure, mobile OS with a sleek and easy to use interface. And all while assessing project risks and providing a status reports to the end of the semester.
Sponsor Information
Tungsten Industries, LLC
Tungsten Industries, LLC is an organization that performs design research and implementation in multiple scientific fields. This includes, but isn't limited to, laser optics, unmanned systems, panoramic imaging, medical, military, and consumer products.
Team Sea Moss
Members
- Current:
- Lyle Johnson
- Computer Science Major
- Encrypted Cloud Storage Researcher
- Adrian Norris
- Computer Science / Mathematics Major
- Mandatory Access Control Researcher
- Former:
- Jon Lamb
- Computer Science Major
- Remote Service Log Retrieval Researcher
Meeting Information
Thursdays from 2:30PM to 3:30PM PST and as needed.
Project Goals
- At the start:
- Research how feasible as well as the process to obtain the following on an Android Mobile Device:
- Encrypted Data Storage
- Remote Service Log Retrieval
- Permission Policy Management
- Create a GUI application for Permission Policy Management
- Current project goals:
- Continue original research
- However, a greater portion of the project focus will shift to permissions policy management and application construction
- Expand and refine the current GUI application
- Develop an IDE for policy building
- Test MAC and Policy Manager on a physical device
- Focus on application interaction and stability
Design Specifications
Expanding on the current goals outlined above.
- Continue Original Research
- Determine the best manner in which to port the encryption function from user to kernel level
- Monitor AppOps progress and the community's response
- Look further in to creating and optimizing permission policies
- Expand and refine the current GUI application
- Establish toolbar functionality
- Add toolbar search and settings features
- Add logic for handling larger than normal application icons
- Add additional aesthetically pleasing features
- Develop an IDE for policy building
- Design the application
- Implement it's core features
- Integrate it into the Policy Manager GUI
- Test MAC and Policy Manager on a physical device
- Ensure the application doesn't take up an unnecessary amount of system resources
- Determine how well other applications hold up during general use with the Policy Manager GUI and permissions in effect
Project Research
- Encrypted Data Storage:
- Current Android implementation: All or nothing view towards encryption
- Includes application, data, downloads, etc.
- Integrated Cloud Storage:
- Implemented in such a way as to require minimum user setup and interaction
- Perhaps only require that a cloud account be verified
- With this built in to the OS the user will gain additional privacy and security at a minimal cost
- Encryption:
- Will require a kernel level function to encrypt/decrypt on the fly
- Redirects sensitive data through system call
- Eventually allow for storing locally or to the cloud
- Remote Service Log Retrieval:
- Uses a Linux style daemon
- Port knocking procedure used to access a device
- Generates a key after each successful login so the device remains secure
- Mandatory Access Controls (MAC):
- AOSP contains the core SELinux MAC
- Optional Middleware MAC functionality will be included
- All requests are denied unless explicitly allowed
- There are currently five types of MMAC to be included:
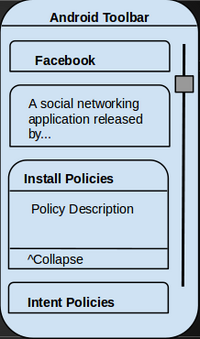
- Install MMAC: Determines if an app may be installed or updated
- Intent MMAC: Checks an app’s intents as they are delivered
- Content Provider: Controls access to structured sets of data
- Permission Revocation: Checks app permissions during runtime
- Enterprise Operations (EOps): Checks app permissions during runtime
- About App Ops:
- App that allows policy permission management
- Hidden release for Android 4.3 and 4.4
- Less verbose with the access controls it employs
Policy Manager Development
- Screen 1 main components complete
- Need to fully implement the toolbar
- Add search functionality
- Add in settings
- Screen 2 main components complete
- Add in settings
- Complete human readable policy display
- Being worked on until mid/late December