UI Cybersecurity Testbed for Power Systems
The goal of this project is to design and implement a virtual display or dashboard that will report cyber-attacks in a meaningful way and test the display through designed and implemented power systems simulations. Documentation of these processes will also be provided for future research.
| [[File:|300px|center|alt=]] | |
| Sponsors | |
| Team Name |
|
| Duration |
|
| Faculty Adviser |
|
| Mentor |
|
| Client |
|
| Team Members |
|
Problem Definition[edit | edit source]
Background[edit | edit source]
Industrial control systems (ICS) and power generation systems need to be reliable, to ensure that power delivery is always available. It has become more prevalent that these systems are vulnerable to cyber-attacks due to the growing complexity of these systems. To solve this, Team SCADACS is working with the University of Idaho (UofI) and Schweitzer Engineering Laboratories (SEL) to help design a cyber security test-bed for power systems. The test-bed will enhance cyber security research by simulating existing power systems and cyber-attacks on critical infrastructure based on the smart grid.
Deliverables[edit | edit source]
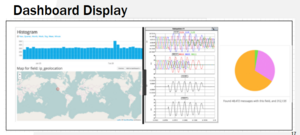
The test-bed will contain an operational dashboard for the simulated power systems which will highlight cyber-attacks for system operators and keep log records of activity. This deliverable will enhance the functionality of the test-bed.
Specifications[edit | edit source]
The scope of this project encompasses further collaborative research between numerous disciplines of engineering involving both graduates and undergraduates.
Design Considerations[edit | edit source]
Functional Requirements[edit | edit source]
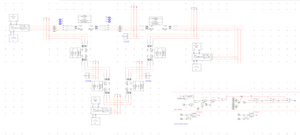
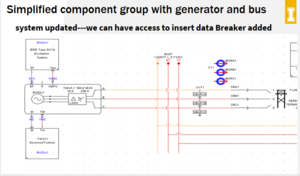
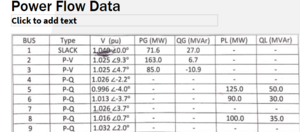
The system shall function where a display or dashboard will harvest information provided off the RTDS, the power racks and SCADA. The information displayed on the dashboard should provide enough security information to a system operator while not overwhelming the system operator with information. The data will consist of information regarding cybersecurity breaches from a simulated power grid. The power grid simulation will be operational using RSCAD as its simulation software and will need to run on the RTDS and power racks. Documentation will need to be provided about the functions of these operations, how they were designed and another necessary information to enhance maintainability for the project and allow for future research and an expanded scope.
Electrical Requirements[edit | edit source]
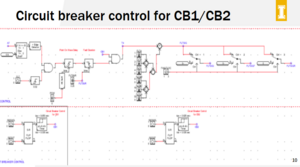
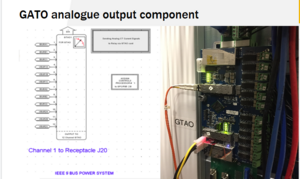
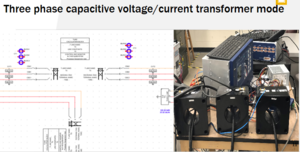
The electrical requirements will include integrating the RTDS, power racks and SCADA equipment with the power test simulations. The power test simulations should use these systems to create the testing environment for the dashboard. It should have documentation of the power test simulations used with the design for future maintenance and use.
Software Requirements[edit | edit source]
The software requirements will involve creating an algorithm to use the data provided from the equipment which will filter out any noise, recognize a cybersecurity threat and alert the system operator to the threat by use of visual display. The visual display needs to be designed so that it is easy to use. It should be easy to navigate for information, shouldn’t overwhelm the operator with data but still provide enough data to handle the situation, and should not lose information in the conversion process between raw data and the visual display. It should have requested features like history logs and provide some form of geographical location information. It should have documentation with the design for future maintenance and use. There will probably be included menus for navigation between log data, color emphases to isolate cybersecurity threats on a virtualized map display using some GIS software, text-based highlights, levels of information in menus such as overviews to low level verbatim data (useful for troubleshooting, maintenance and finding out more details about the threat).
Regulatory Requirements[edit | edit source]
This software and hardware will be used in accordance with the restrictions provided by the grants and shall be used for educational and research purposes. Each individual working on this project is expected to work professionally in accordance with the ethical restrictions placed on each degree by certified organizations. For example, computer science and electrical computational engineering students will abide by the ethical restrictions imposed by ACM, IEEE, ISSA, EC under the following codes of ethics: ACM Codes of Ethics and Professional Conduct, IEEE Code of Ethics, ISSA Code of Ethics, EC Council Code of Ethics.
Cost Requirements[edit | edit source]
The budget mainly comes through grants from the University of Idaho and Murdock Trust. SEL is also subcontracted to provide equipment. The grants are sponsored to promote research in areas of critical infrastructure. As such, budget requests must comply by the requirements specified by the grants and the correct procedures must be followed when requesting funds. Budget requests can be made through Brian Johnson on the Thursday client meetings. Our project has very minimal cost requirements. Most of the hardware equipment needed has already been purchased and so there is no need to purchase any additional hardware. To help promote availability, our group will use open source software or else develop our software to fulfill the tasks required. There is a buffer budget of $500.00 for any unforeseen expenses, regarding software licensing, or lab key deposits. We also have budgeted $100.00 for our expo display supplies. Other cost requirements will include producing a functional design that doesn’t incorporate any unnecessary cost into the project. Labor costs for lab usage, software development, simulation development, testing and documentation are set at $0.00/hr because it doesn’t directly factor into our budget due to the nature of the project.
Project Learning[edit | edit source]
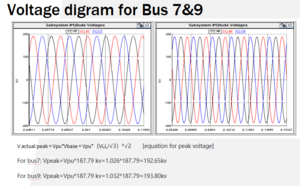
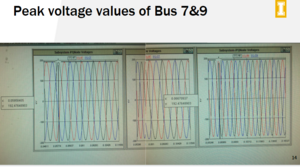
Learning how to use the RSCAD software from provided tutorials for electrical system modeling. These tutorials will provide the framework to create a 9 bus electrical system which we will be using as a research and testing model for the cyber security analysis and dashboard display functionality. Technical knowledge will come from learning about network interfacing, the SCADA devices and equipment functionality (RSCAD, RTDS, RTAC) including thesoftware it uses to function. Other security related standards such as DPN3 and development resource tools such as GIS software for the dashboard display.
Soft skills include learning how to integrate with other previous research and progress that has already been developed for this project.
Before the decision of graylog and scadabr, there were also options of elk and security onion so there was some research into functionality with those log and security tools as well. The CS students have been busy integrating several requested logging tools and HMI interfaces together into one dashboard configuration. They have learned about the functionality of these tools (Graylog and scadaBR), Virtual Machines (VMware) and memory requirements, Network Configurations and IP protocols, and the overall system structure of the testbed including how to interface our dashboard with the equipment to pull data. We have also learned about control system hardware its integration with the real time digital simulator and relays and basic power simulations. We have developed an understanding of how the system models and actual power grid and the importance of creating a dashboard to detect cyber related attacks on the simulated system for future research.
Link to Graylog Documentation: http://docs.graylog.org/en/3.0/ Link to SCADABR Documentation: https://sourceforge.net/p/scadabr/wiki/Manual%20ScadaBR%20English%200%20Summary/
Final Design[edit | edit source]
Validation[edit | edit source]
Team Members[edit | edit source]
All group members also have a role to participate in the project on a fundamental level using their expertise in electrical engineering and computer science.Additional Documentation[edit | edit source]
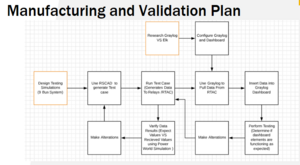
Design Validation Plan[edit | edit source]
File:SCADACS14ValidationPlan.pdf
Project Schedule[edit | edit source]
Budget[edit | edit source]
Meeting Minutes[edit | edit source]
File:942018MeetingMinutesSCADACS14.pdf
File:SCADACS14MeetingMinuteTemplate.pdf
File:SCADACSMeetingAgendaSep13ToOct4.pdf
[[File:]]
[[File:]]
[[File:]]
[[File:]]
Presentations[edit | edit source]
[[File:]] [[File:]] [[File:]] [[File:]]