Plug and Play Home Energy Generation with Secure IoT control
| Sponsors | UI Facilities and Prof. Herb Hess
|
| Team Name | Sunbeam |
| Duration | Spring 2019 - Fall 2019 |
| Faculty Adviser | |
| Client | Prof. Herb Hess
|
| Team Members |
|
The goal of team SunBeam is to design a system to allow a user plug and play remote access to their personal solar generation system. To do this, we altered an Inergy Kodiak 1100W Solar Generator from within. When unmodified, the Kodiak does provide useful information via an LCD screen attached to the device, but loses all historical data as soon as it stops charging or is powered off. The task of integrating the Kodiak completely is outside the scope of what the time allowed, so we focused mainly on getting information from the Kodiak in a way that could be easily utilised in an IoT application. Using sensors both within and outside of the chassis, we add useful functionality to the generator such as long term statistics, remote access, and real time readings on the state of the system. We hope that our work on this project will lay the foundation for future teams by creating an interface with outside sensors and recording vital information about the voltage and current of the generator.
Problem Definition[edit | edit source]
The goal of our project is to add IoT functionality to an existing solar generator, which includes real time monitoring, statistic recording, and remote access. We also aim to accommodate future I/O features.
Background[edit | edit source]
Small scale solar generation has many benefits, but often it just comes down to two: convenience and money. Our project aims to modify a product designed to be easy to use so that its easier to understand and even more convenient.
Imagine a person with a small solar setup going camping for a few weeks with their RV in the middle of nowhere. If they have a solar setup with a Kodiak generator, there are a few ways IoT integration could be of real use.
For example, when using power during the night, there is no way to know how much charge the battery has left other than to check the system itself. If they were to go for a hike and forgot the lights on, they wouldn’t be able to do anything about it. IoT integration could solve these problems. Our system could potentially push a notification to the user’s phone when they only have a few hours of power left, or could allow them to toggle power output on and off. To open this world of opportunities, we needed to get information into a usable state that could be easily integrated with IoT.
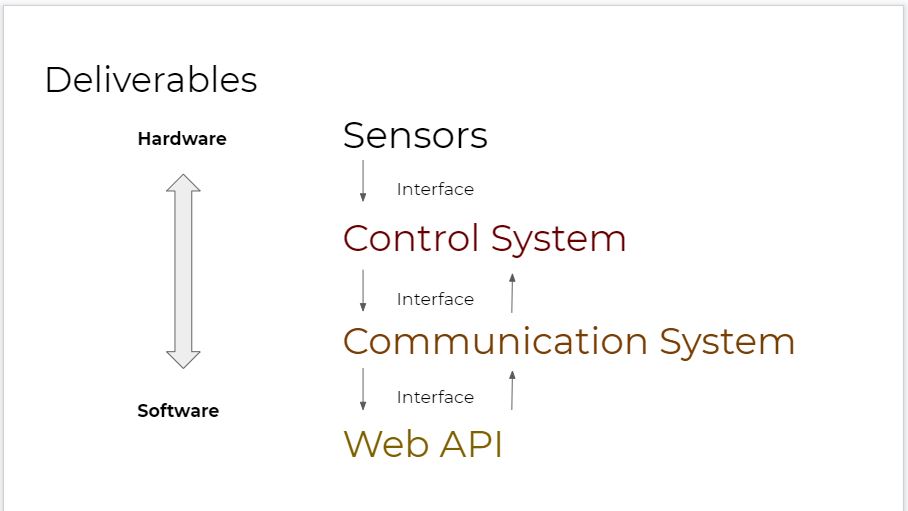
Deliverables[edit | edit source]
1. Design will integrate Custom Circuits with a modern IoT standard
2. Robust IoT Security - Defined and tested after prototype is developed
3. State Reporting - Gather information from environment and securely deliver to user
4. Control Signals - Can securely receive information from end users, such as requesting information from specific dates
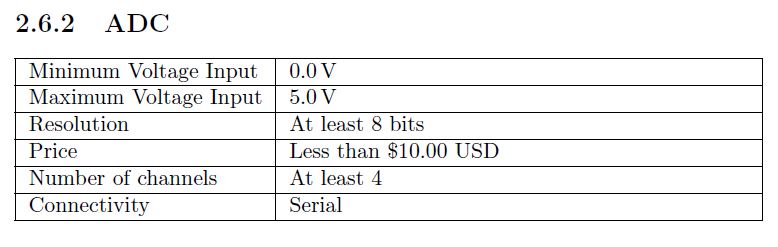
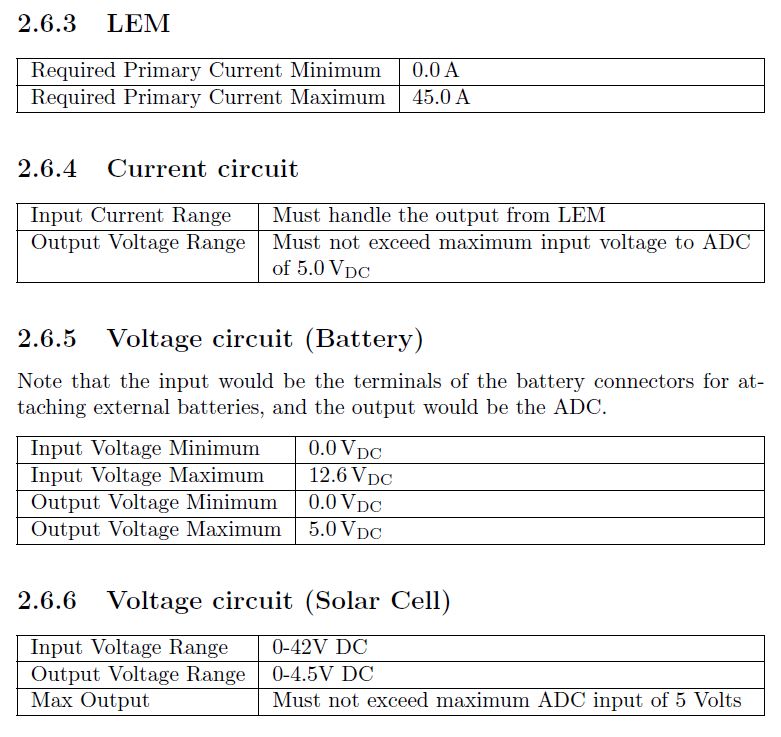
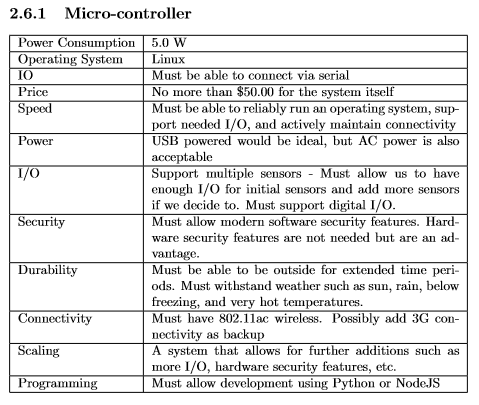
Specifications[edit | edit source]
Requirements:
Connectivity - Must fit ‘plug and play’ description. Should have wireless connectivity without requiring special installation.
Security: We will create a threat model and upgrade our design in accordance to that.
Design Considerations[edit | edit source]
We will design a system that gives a customer access and control over their home solar energy generation and power. The user will be able to see things such as the current power being generated, the light conditions outside, and the temperature. They will be able to control things such as ...
We will approach this with three goals in mind. Secure remote control Control system Sensors
Project Processing[edit | edit source]
Design Process
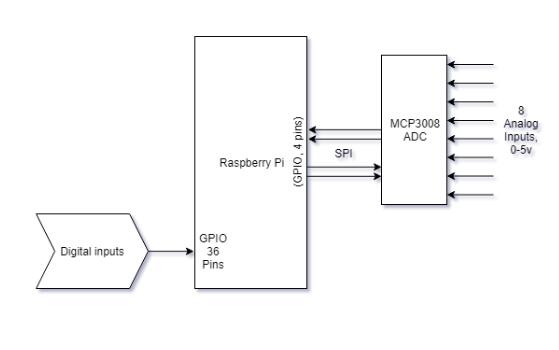
What we desire to do with Raspberry Pi[edit | edit source]
Detect the temperature Show the value of current & voltage
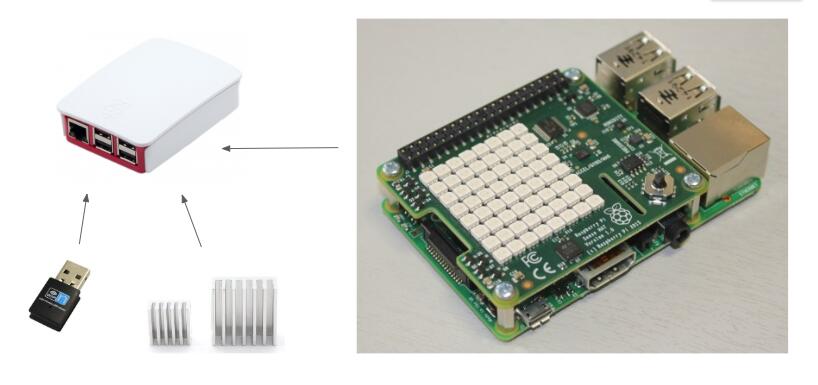
What does the Rasberry PI look like?
What does the Solar Panel and Kodiak Solar Generator look like?
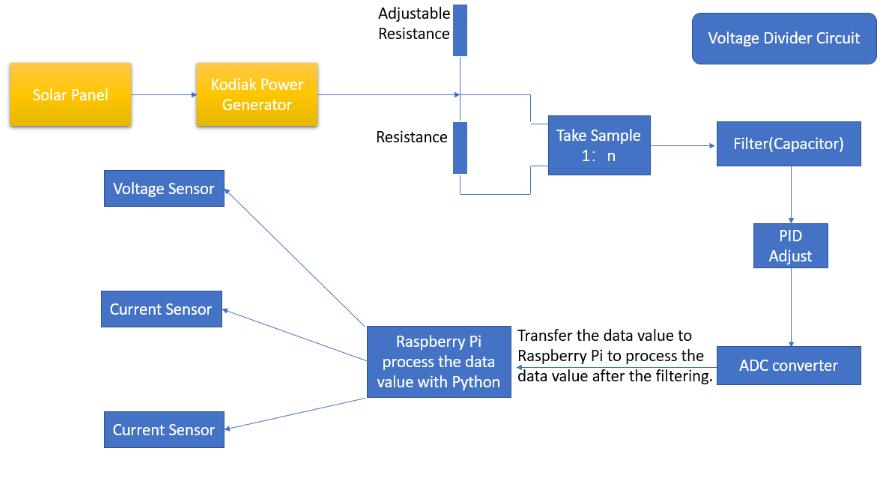
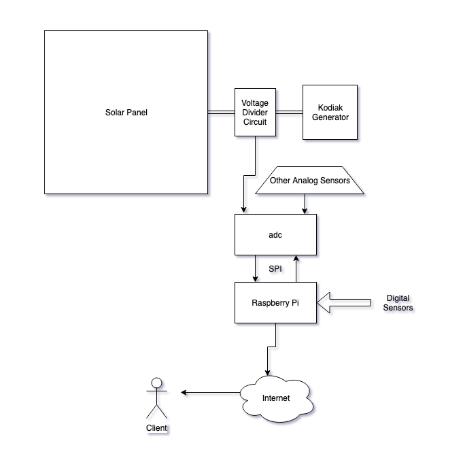
The general schematic of the project
The specific schematic of the project with the parts
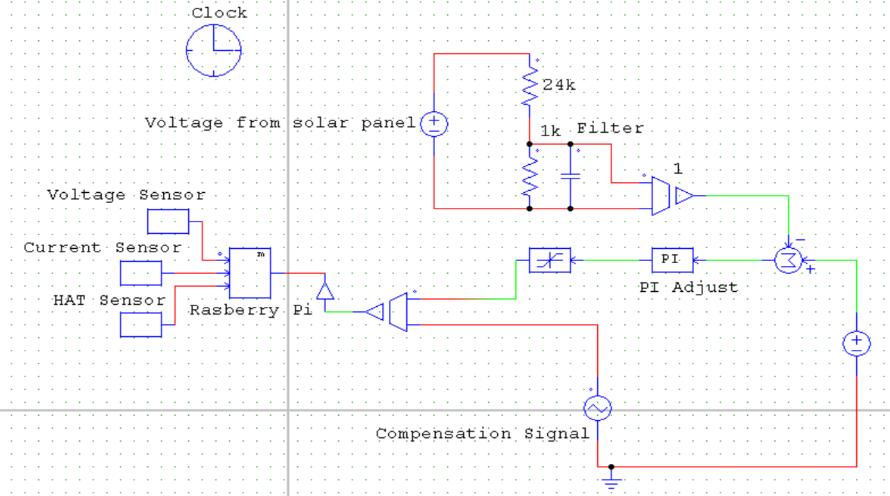
The circuit schematic of the project with the parts
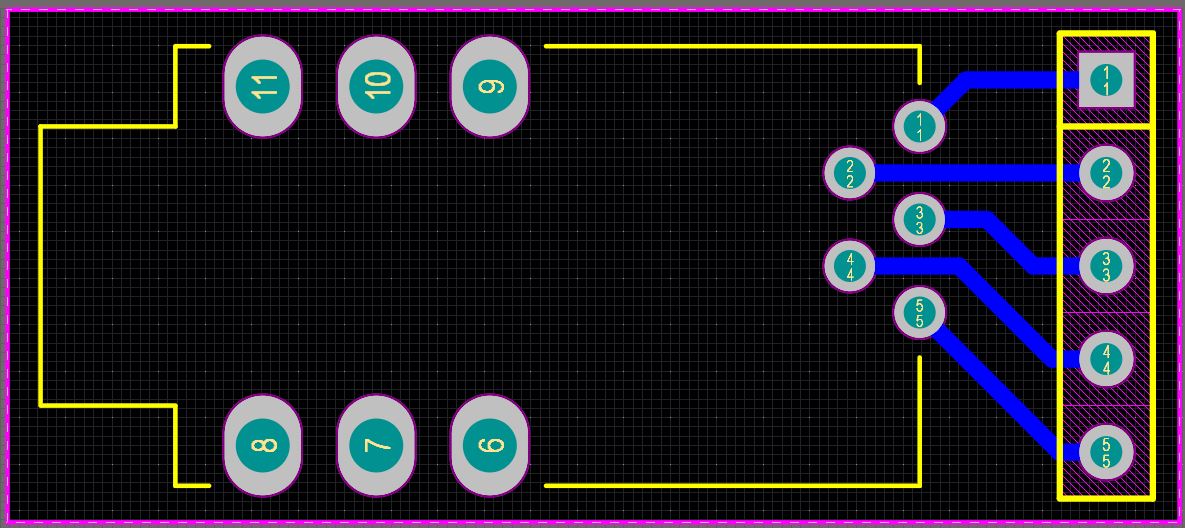
LEM PCB Soldering
The datasheet of ADC sensor
Design Steps
Final Design[edit | edit source]
The general ideal of the project
Validation[edit | edit source]
Threat Model
Introduction
One of the main goals we would like to measure our success in this project is our implementation of security features. To do this we need to define what the most likely exploits to our system are and the many ways we could prevent those exploits from being used. This threat model lists the possible points of interest in our system, how vital they are to the security of our device, and ways me might prevent them.
There are 4 stages to effectively addressing security:
-Model the application
-Enumerate Threats
-Mitigate threats
-Validate the mitigations
Part 1: Physical security
-Safety features
-Power storage
Part 2: Data security
-Vital Data
-Data Storage
Part 3: Network security
-Network Communications
-Third Parties
-Authentication
Team Members[edit | edit source]
| Derek Mitten
Major: Computer Engineering
| |
| Pengfei Chen
Major: Electrical Engineering
| |
| Zihao Huang
Major: Electrical Engineering
|
Additional Documentation[edit | edit source]
Project Schedule
Budget
Snapshot
Agenda
Meeting Minutes
Presentations
Design Review
GitHub
Final Report
Final Poster